How to Boost Node.js Security to Prevent SEO Spam Attacks
Node.js is a powerful and popular server-side scripting language that is used to build websites and web applications. It is a great choice for developers who want to create fast, secure, and scalable web applications.
Table of content
Table of Contents
We’re on board to help with your product. Don’t hesitate to get in touch.
Contact Us Let’sTalk
Node.js is a powerful and popular server-side scripting language that is used to build websites and web applications. It is a great choice for developers who want to create fast, secure, and scalable web applications.

However, it is important to understand the security implications of using Node.js and how to properly secure your Node.js applications to prevent SEO spam attacks. In this article, we’ll discuss the basics of Node.js security, what SEO spam attacks are, how to boost Node.js security, and best practices for preventing SEO spam attacks
Introduction to Node.js Security
Node.js is an open-source server-side JavaScript language that is used to create web applications. It is popular for its scalability, performance, and security. It provides developers with a variety of tools and frameworks to quickly and easily create powerful web applications.
However, with the power of Node.js comes the responsibility of ensuring that your applications are secure. No matter how powerful a language is, there will always be vulnerabilities that can be exploited. Therefore, it is important to understand the basics of Node.js security and how to secure your Node.js applications.
Node.js comes with built-in security features such as access control, data encryption, and authentication. However, these features are not always enough to prevent malicious actors from exploiting your application. Therefore, it is important to understand the different types of security threats that can affect Node.js applications and how to properly secure your Node.js applications.
What Are SEO Spam Attacks?
SEO (Search Engine Optimization) spam attacks are a type of malicious attack that aims to manipulate search engine rankings. These attacks are designed to inject malicious links and content into websites in order to manipulate the rankings of the targeted website.
SEO spam attacks can be devastating for businesses, as they can cause a website to be blacklisted by search engines, resulting in a loss of traffic and revenue. In addition, these attacks can be difficult to detect and remove, as malicious actors can use sophisticated techniques to bypass security measures.
Therefore, it is important to understand the different types of SEO spam attacks and how to prevent them from affecting your Node.js applications.
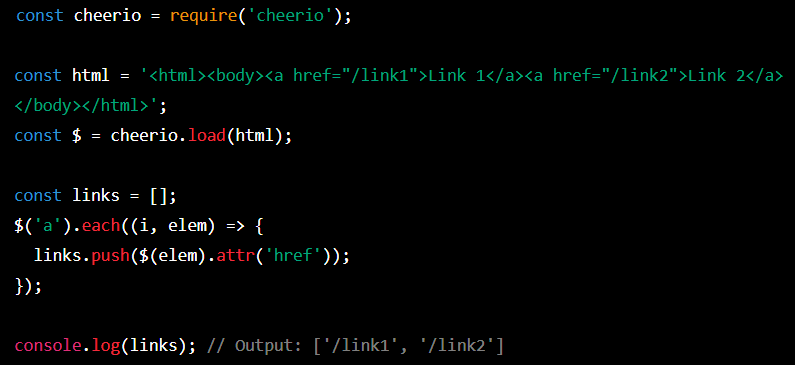
The code uses the cheerio library, which allows you to use selectors and functions similar to those available in jQuery to process HTML. In this case, the
$('a')selector returns allaelements in the HTML document. Theeachfunction is then used to iterate over these elements and a function is called which retrieves thehrefattribute of each element and adds it to thelinksarray.Finally, the code displays the contents of the
linksarray using theconsole.logfunction.
How to Boost Node.js Security
In order to ensure the security of your Node.js applications, there are several steps that you can take to boost your Node.js security.
The first step is to ensure that all of the components of your Node.js application are up to date. This includes the Node.js runtime, any third-party modules, and any other software that is used in your application. By keeping all of the components of your application up to date, you can ensure that any security vulnerabilities that have been identified and patched in the newer versions of the software are not present in your application.
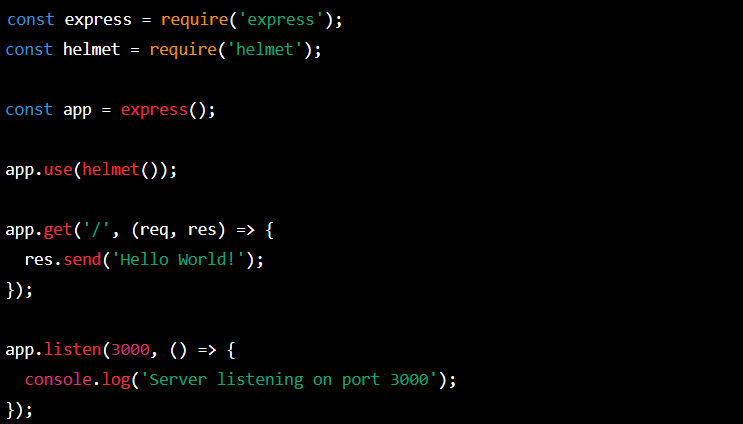
The code starts by importing two libraries – express and helmet. Then, a new app object is created using the express function. The app then uses the helmet middleware, which protects the app from some known network attacks.
Next, the app sets up handling for HTTP GET requests based on the main URL (‘/’). When someone sends a GET request to this URL, the app sends a response “Hello World!” back to the browser.
The use of helmet middleware can help secure applications against some known network attacks, such ascross-site scripting (XSS) andclickjacking attacks.
Finally, the code sets the app to listen on port 3000 and displays a message in the console when the app is ready to receive requests.
The next step is to use secure coding practices. This includes using best practices such as input validation and output encoding, using secure libraries and frameworks, and ensuring that your code is well tested and maintained.
In addition, it is important to use secure authentication and authorization methods. This includes using strong passwords, using two-factor authentication, and using secure tokens. It is also important to encrypt data that is stored in your Node.js applications, as this can help prevent malicious actors from accessing sensitive information.
Finally, it is important to use secure libraries and frameworks. There are a variety of open-source Node.js libraries and frameworks that you can use to secure your Node.js applications.
Securing Your Node.js Application
Once you have taken the necessary steps to boost your Node.js security, it is important to secure your Node.js application. This includes implementing a secure development lifecycle, using secure coding practices, and testing your application regularly.
The secure development lifecycle is a process that involves planning, developing, testing, and deploying secure applications. This process ensures that any security issues that are identified during the development process are addressed before the application is released.
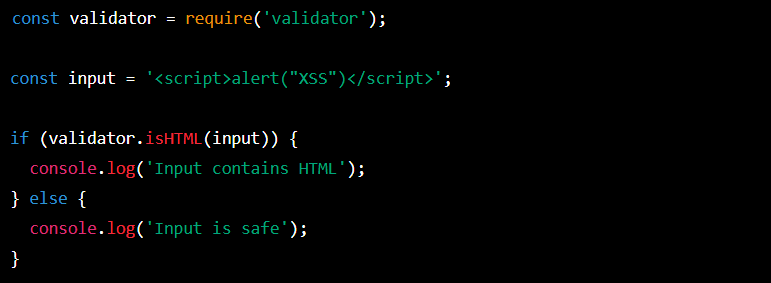
The code uses the validator library to check whether the string is valid HTML code. If it is, the
Checking whether a string contains HTML code is one way to protect applications fromisHTMLfunction returns true, otherwise it returns false. Depending on what this function returns, the appropriate message is displayed in the console.In this specific case, theinputstring contains HTML code, so theisHTMLfunction will return true and “Input contains HTML” will be displayed in the console.XSS attacks.
In addition, it is important to use secure coding practices such as input validation and output encoding. This ensures that any malicious input is rejected and that any output is properly encoded. This can help to prevent malicious actors from exploiting your application.
Finally, it is important to test your application regularly. This includes using automated security testing tools to identify any security vulnerabilities that may exist in your application. This can help to ensure that any security vulnerabilities that are identified are addressed before they can be exploited.
Security Tools for Node.js
There are a variety of security tools that can be used to secure Node.js applications. These tools can help to identify and address any security vulnerabilities that may exist in your application.
The first tool is the Node Security Platform (NSP). This is a security tool that can be used to identify any security vulnerabilities that exist in your Node.js application. The NSP will scan your application and identify any security issues. It will then provide recommendations on how to address any security issues that are identified.
In addition, there are a variety of open-source security tools that can be used to secure Node.js applications. These tools can be used to identify and address any security vulnerabilities that may exist in your application.
Finally, there are a variety of third-party security tools that can be used to secure Node.js applications. These tools can help to identify and address any security issues that may exist in your application.
Security Auditing for Node.js Applications
Examining the security of your Node.js applications is a significant task. Security auditing consists of examining your application to recognize any safety risks that could be present. It is essential to routinely audit your Node.js applications, as this can help to guarantee that any security flaws that are found are taken care of before they can be exploited.
There are a variety of tools that can be used to audit Node.js applications. These tools can be used to identify any security issues that may exist in your application. The most common security auditing tools are static analysis tools, dynamic analysis tools, and vulnerability scanning tools.
Static analysis tools can be used to analyze the source code of your application to identify any security issues that may exist. Dynamic analysis tools can be used to analyze the behavior of your application to identify any security issues that may exist. Finally, vulnerability scanning tools can be used to scan your application for any known vulnerabilities.
Best Practices for Node.js Security
In addition to using security tools to secure your Node.js applications, there are a variety of best practices that you can use to ensure the security of your Node.js applications.
The first best practice is to use a secure coding standard. This ensures that any code that is written for your application follows best practices for security.
The second best practice is to use secure authentication and authorization methods. This includes using strong passwords, using two-factor authentication, and using secure tokens.
The third best practice is to use secure libraries and frameworks. This includes using open-source libraries and frameworks that are actively maintained and updated.
The fourth best practice is to use secure storage and encryption. This includes using secure storage systems such as databases and using encryption to protect any sensitive data that is stored in your application.
Finally, it is important to use secure communication protocols. This includes using secure protocols such as SSL/TLS to protect any data that is sent between the client and the server.
How to Monitor Node.js Security
It is important to monitor your Node.js applications for any security issues that may arise. This includes monitoring for any security vulnerabilities that are identified and any suspicious activity that may be taking place in your application.
There are a variety of tools that can be used to monitor Node.js applications for security issues. These tools can be used to monitor for any security vulnerabilities that are identified, any suspicious activity that is taking place in your application, and any changes to your application’s code.
In addition, it is important to monitor your application’s performance. This includes monitoring for any performance issues that may arise and any changes to your application’s performance.
Finally, it is important to use logging and monitoring tools to monitor your application’s security. These tools can be used to monitor for any security issues that may arise and any suspicious activity that may be taking place in your application.
How to Respond to Security Breaches
In the event of a security breach, it is important to respond quickly and effectively. This includes identifying the source of the breach, taking steps to contain the breach, and taking steps to prevent future breaches.
The first step is to identify the source of the breach. This can be done by analyzing the logs of your application and any other relevant data. Once the source of the breach has been identified, it is important to take steps to contain the breach. This includes disabling any malicious accounts, resetting passwords, and revoking any access tokens.
The next step is to take steps to prevent future breaches. This includes implementing security best practices, using secure coding practices, and using secure authentication and authorization methods. It is also important to use secure storage and encryption methods and to use secure communication protocols.
Finally, it is important to use security tools to monitor your application for any security issues that may arise. This includes using security auditing tools to identify any security issues that may exist in your application and using security monitoring tools to monitor for any suspicious activity that may be taking place in your application.
Conclusion
Node.js is a powerful and popular server-side scripting language that is used to build websites and web applications. However, it is important to understand the security implications of using Node.js and how to properly secure your Node.js applications to prevent SEO spam attacks. In this article, we discussed the basics of Node.js security, what SEO spam attacks are, how to boost Node.js security, and best practices for preventing SEO spam attacks.
By taking the necessary steps to secure your Node.js applications, you can ensure that your applications are safe from SEO spam attacks. This includes using secure coding practices, using secure authentication and authorization methods, using secure libraries and frameworks, and using security tools to monitor your applications for any security issues that may arise.
By following these best practices, you can ensure that your Node.js applications are secure and protected from SEO spam attacks.


